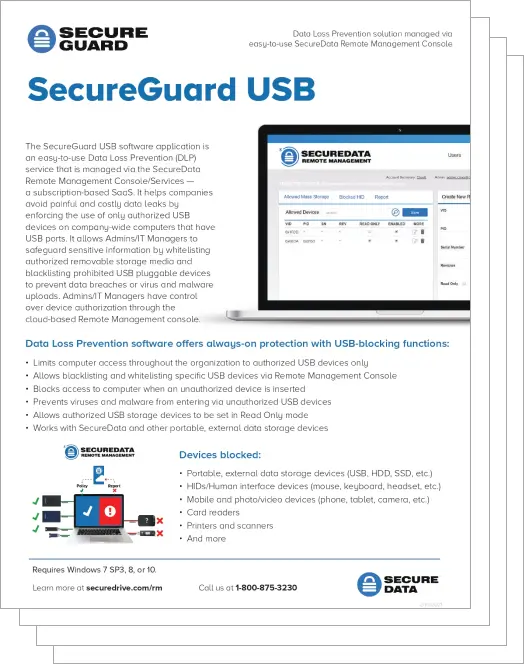
The SecureGuard USB software application is an easy-to-use Data Loss Prevention (DLP) service that is managed via the SecureData Remote Management Console/Services—a subscription-based SaaS. It helps companies avoid painful and costly data leaks by enforcing the use of only authorized USB devices on company-wide computers that have USB ports. It allows Admins/IT Managers to safeguard sensitive information by whitelisting authorized removable storage media and blacklisting prohibited USB pluggable devices to prevent data breaches or virus and malware uploads. Admins/IT Managers have control over device authorization through the cloud-based Remote Management console.
It safeguards sensitive information by whitelisting and blacklisting USB devices for computers with the program installed, including:
- Portable, external data storage devices (USB, HDD, SSD, etc.)
- HIDs/Human interface devices (mouse, keyboard, headset, etc.)
- Mobile and photo/video devices (phone, tablet, camera, etc.)
- Card readers
- Printers and scanners
- And more
When an unauthorized device is inserted into a USB port, the program blocks the user from accessing all computer functions until the device is removed.
How it works…
- Step 1: Set up Remote Management account and download software pack from link provided
- Step 2: Install on computers throughout organization
- Step 3: Authorize devices allowed for use
Login and Management
Downloadable after purchase and easy installation on all computers. An Admin must authenticate during installation of SecureGuard USB using the same credentials from their Remote Management Account. Once the program is installed, the target computer will automatically appear in the Remote Management Account for convenient and easy management.
Remote Management
Remote Management (RM) allows Admin to manage SecureGuard USB through the internet from a remote computer. It is a user-friendly interface that allows remote control and management of the program on all computers with SecureGuard USB installed on them. RM provides Admin with a console for easy management and accessing details.
RM Console
Through RM, Admin can whitelist or blacklist devices by Vendor ID, Product ID, Serial Number or Revision. Only devices allowed by Admin can be used on a host computer. Admin has control over allowed devices and can view detailed reports of port activity on individual computers. RM features a Create New Record field to easily add devices to the whitelist or blacklist. With one click, Admin can easily remove whitelisted devices, which will go into effect within seconds. Admin can also customize authorized drives to access files in Read Only mode.
Access Log
The Report feature tracks all uses of an external drive on an individual computer, whether it is blacklisted or whitelisted. The access log shows detailed USB data, including date and time used, device type, identification numbers and if the program blocked or allowed the device. Note: data stored on external devices is not visible to Admin.